


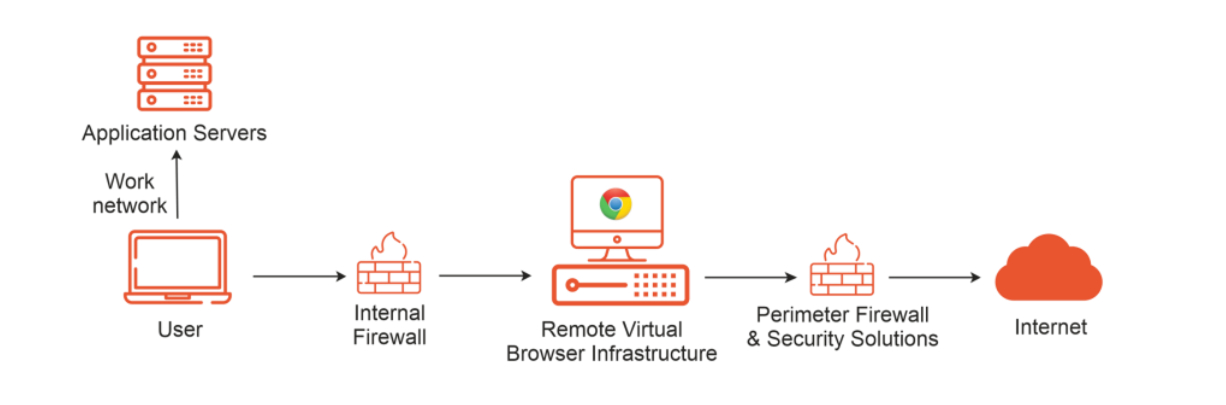
Multi-Tenant or Dedicated:
Deploy shared containers for cost efficiency or carve out single-tenant VMs for the highest compliance needs.
GPU-Accelerated Rendering:
Deliver near-native performance for rich web applications, even on thin clients.
Granular Controls:
Define URL categories, file-download rules, clipboard restrictions, and user roles from a single Accops Console.
DLP & Compliance:
Enforce GDPR, PCI-DSS, and HIPAA data leak prevention policies directly at the browser layer.
Identity & Access:
Leverage your existing SSO (SAML, OAuth) and MFA stack for transparent user authentication.
SIEM & Analytics:
Forward detailed session logs and real-time alerts (Syslog) into the SIEM of choice.
Auto-Scaling Containers:
Dynamically spin up or tear down browser instances to match demand, eliminating idle infrastructure costs.
Thin-Client Compatibility:
Support legacy desktops, zero-clients, and mobile devices with no endpoint software installation.




Zero Trust Browsing:
Every session is ephemeral. Even zero-day exploits are confined and eradicated at session teardown.
Phishing & Malware Defence:
Automatically isolate all email links and untrusted web traffic—neutralizing threats before they ever touch your network.
Data Sovereignty:
To satisfy local regulations and internal policies, keep session data within regional data centres.
Audit-Ready Reporting:
Comprehensive session playback, file transfer logs, and user-activity trails simplify audits and investigations.
Device-Agnostic Access:
Users can browse securely from any platform—Windows, macOS, Linux, iOS, Android, or thin clients.
No Local Agents:
Eliminate endpoint patching and browser-extension headaches—security is delivered entirely from the centralised setup.
Data Protection:
Restrict users from downloading or uploading content to the local machine, copy/paste, screen recording, etc., to give enhanced control over user activities and create an air-gapped browsing environment.
Centralized Management:
One console to govern browsing policies, monitor health, and roll out updates—freeing up IT resources.

